In today’s increasingly interconnected digital landscape, securing access to sensitive data and applications has become paramount. As organizations embrace cloud-based solutions, the need for robust access control mechanisms has never been greater. Google Cloud Identity-Aware Proxy (IAP) emerges as a powerful tool to address this challenge, providing a centralized and granular approach to safeguarding cloud resources.
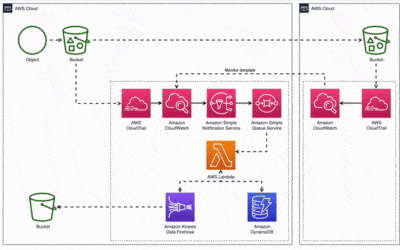
While working on an open source DQM [Data Quality Monitor] frontend and backend, I had chosen IAP to secure the frontend of this DQM tool. To secure and control access to the front end, I did not have to create any login page, instead authorization and authentication were completed and taken care of by IAP itself. You can refer to the below design for DQM.
Understanding IAP’s Role in Cloud Security
IAP acts as a gatekeeper, intercepting all traffic destined for your cloud
applications and enforcing access policies based on user identities and contextual factors. It eliminates the need to expose applications directly to the internet, shielding them from unauthorized access and potential attacks. This approach aligns with the Zero Trust model, emphasizing the principle of “never trust, always verify” for every access request.

Key Features that Enhance Cloud Protection
IAP boasts a comprehensive set of features that elevate cloud security to new heights:
- Centralized Access Control: Manage access policies from a single console, ensuring consistency and simplifying administration.
- Granular Access Levels: Define fine-grained access rules based on user groups, attributes, and contextual factors, such as device type and location.
- Application-Level Security: Protect applications hosted on Google Cloud, other cloud providers, or even on-premises infrastructure.
- TCP Forwarding: Secure SSH and RDP connections to VMs without exposing them to public IP addresses.
- Integrated Authentication: Leverage existing identity and access management (IAM) solutions, such as Google Cloud IAM or Active Directory, for seamless authentication and authorization.
Real-World Benefits of Implementing IAP
Adopting IAP brings a multitude of benefits to cloud environments:
- Enhanced Security: Reduce the risk of data breaches and unauthorized access by enforcing stringent access controls.
- Simplified Management: Centralize access policy management and streamline user provisioning.
- Improved User Experience: Provide users with a secure and consistent access experience across all applications.
- Reduced Operational Costs: Eliminate the need for VPNs and simplify network management.
A User’s Perspective on IAP Implementation
As a user, I’ve found IAP to be a valuable tool for securing my cloud applications. Its centralized approach and granular access controls have significantly improved the overall security posture of our organization. The integration with existing IAM solutions has made the implementation process seamless, and the overall user experience has been positive.

Conclusion: A Powerful Ally in Cloud Security
Google Cloud IAP stands as a testament to Google’s commitment to providing robust security solutions for cloud environments. Its comprehensive features, ease of implementation, and tangible benefits make it a compelling choice for organizations seeking to safeguard their valuable data and applications. Whether you’re a seasoned cloud administrator or just starting your cloud journey, IAP is an invaluable tool to enhance your organization’s cloud security posture.



0 Comments